17 Dec Contact Form 7 Vulnerability in +5 Million Sites via @martinibuster
A vulnerability has been discovered in Contact Form 7 that allows an attacker to upload malicious scripts. The publishers of Contact Form 7 have released an update to fix the vulnerability.
Unrestricted File Upload Vulnerability
An unrestricted file upload vulnerability in a WordPress plugin is when the plugin allows an attacker to upload a web shell (malicious script) that can then be used to take over a site, tamper with a database and so on.
A web shell is a malicious script that can be written in any web language that is uploaded to a vulnerable site, automatically processed and used to gain access, execute commands, tamper with the database, etc.
Contact Form 7 calls their latest update an “urgent security and maintenance release.”
“An unrestricted file upload vulnerability has been found in Contact Form 7 5.3.1 and older versions.
Utilizing this vulnerability, a form submitter can bypass Contact Form 7’s filename sanitization, and upload a file which can be executed as a script file on the host server.”
A more detailed description of the vulnerability was published on Contact Form 7’s WordPress plugin repository page.
These are the additional details about the vulnerability that was shared on the official WordPress plugin repository for Contact Form 7:
“Removes control, separator, and other types of special characters from filename to fix the unrestricted file upload vulnerability issue.”
Screenshot of WordPress Plugin Changelog Update Description
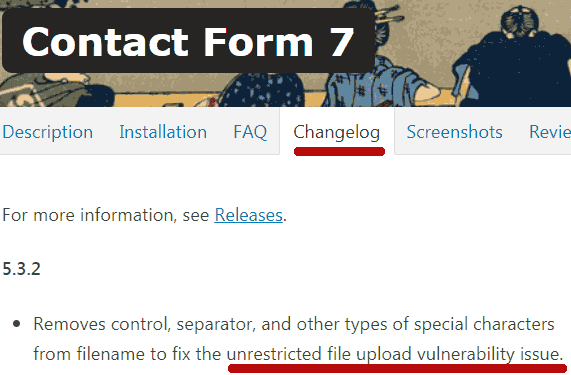

The screenshot above is of the Contact Form 7 plugin “more info” description that is shown when updating the plugin from a WordPress installation. The wording matches what is published on the official WordPress repository for the plugin.
Filename Sanitization
Filename sanitization is a reference to a function related to scripts that process uploads. Filename sanitization functions are designed to control what kinds of files (file names) are uploaded by restricting certain kinds of files. Filename sanitization also can control file paths.
A filename sanitization function works by blocking certain file names and/or allowing only a restricted list of file names.
In the case of Contact Form 7, there was an issue in the filename sanitization which created the situation where certain kinds of dangerous files were unintentionally allowed.
Vulnerability Fixed in Contact Form 7 Version 7.5.3.2
The vulnerability was originally discovered by researchers at Web Security company Astra.
The filename sanitization vulnerability exploit is fixed in Contact Form 7 version 7 5.3.2.
All versions of Contact Form 7 from 7 5.3.1 and under are considered vulnerable and should be updated immediately.
Citations
Read announcement at Contact Form 7
https://contactform7.com/2020/12/17/contact-form-7-532/
Read announcement at Security Company Astra
Unrestricted File Upload Vulnerability found in Contact Form 7
Read the Contact Form 7 Changelog
Sorry, the comment form is closed at this time.