31 Mar Critical Vulnerability in Rank Math SEO Plugin via @martinibuster
Rank Math SEO plugin was discovered to have a critical vulnerability. The vulnerability could allow an attacker to gain administrative access. The issue was fixed one day after Rank Math was notified.
Privilege Escalation Vulnerability
Privilege escalation in the context of a WordPress site is a reference to a situation like a coding bug that creates an opportunity for an attacker to gain higher access, up to administrator level privileges.
In the Rank Math exploit that was discovered, any registered user could exploit this flaw and gain administrator privileges.
Once a hacker has obtained administrator privileges they can do a variety of things, including deleting an administrator and creating a new one.
According to the WordPress Vulnerability Database:
“This plugin registered a REST-API endpoint, rankmath/v1/updateMeta, which failed to include a permission_callback used for capability checking.”
The permission_callback verifies that the user performing the action has the permission to perform the action.
This is how the official WordPress developer documentation describes the importance of the permission_callback:
“This is a function that checks if the user can perform the action (reading, updating, etc) before the real callback is called. This allows the API to tell the client what actions they can perform on a given URL without needing to attempt the request first.”
What that appears to say is that the permission_callback that checks if the user has the correct permission is supposed to be there but it was missing.
WordFence refers to the lack of a permission_callback a failure:
“In order to add this feature, the plugin registered a REST-API endpoint, rankmath/v1/updateMeta, which failed to include a permission_callback used for capability checking.
…The WordPress SEO Plugin – Rank Math plugin includes a number of optional modules, including a module that can be used to create redirects on a site.
In order to add this feature, the plugin registered a REST-API endpoint… which again failed to include a permission_callback for capability checking.”
The WordPress Vulnerability Database stated that the failure to add a permission_callback could allow an attacker to delete an administrator or grant administrator privileges to a registered user.
“This endpoint also allowed for updating metadata for users. WordPress user permissions are stored in the usermeta table, which meant that an unauthenticated attacker could grant or revoke administrative privileges for any registered user.”
These Versions of Rank Math are Vulnerable
At this time, any version of Rank Math lower than 10.0.41 is vulnerable to an attack.
It is highly recommended that users update their Rank Math SEO plugin to the latest version
Rank Math Responded Quickly
Rank Math learned of the vulnerability on March 25, 2020. An update to fix the vulnerability was issued the next day, March 26, 2020.
Rank Math fixed the problem in a timely and responsible manner.
Did Rank Math Notify Users About the Problem?
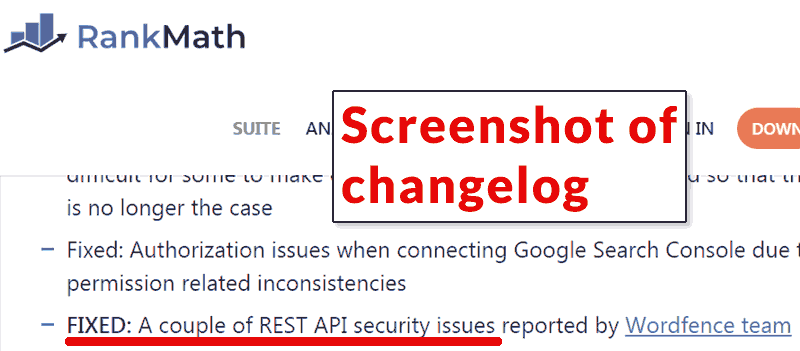
Yes, Rank Math operated in a transparent manner. Their changelog contains a note that they fixed a security issue. This is great that the Rank Math team did that and it shows they are responsible developers.
This is what the official Rank Math changelog describes the fix:
“FIXED: A couple of REST API security issues reported by Wordfence team”

Rank Math Handled Problem Responsibly
The Rank Math team were honest about the issue and responded quickly to solve the problem.
Some developers try to hide what was fixed and use opaque phrases about fixing something without actually saying it was a security issue.
So I have to commend Rank Math for being transparent. Their swift response and transparency about what they are fixing inspires confidence in their plugin.
WPVULNDB description of the vulnerability
The official WordFence description of the critical vulnerability.
Sorry, the comment form is closed at this time.