15 Jul Critical Vulnerability Strikes WordPress Ad Inserter via @martinibuster
Ad Inserter, a popular Ad management WordPress Plugin was discovered to contain a critical vulnerability. The vulnerability allows an authenticated user as low as a subscriber to execute code on the affected website. It is advised that users of the plugin update immediately.
 This is a screenshot of the WordPress dashboard. In the top left hand corner is a link that allows you to update your plugins.
This is a screenshot of the WordPress dashboard. In the top left hand corner is a link that allows you to update your plugins.Description of Ad Inserter Vulnerability
There are actually two vulnerabilities.
Authenticated Path Traversal Exploit
The first vulnerability is called an Authenticated Path Traversal Exploit. This exploit exists in Ad Inserter version 2.4.19 and under.
This is a type of exploit that allows an attacker to access to areas of a site by adding variables to the URL, variables like ../. This allows an attacker to “traverse” to an area that may allow them to execute code or see private information.
According to Common Weakness Enumeration (CWE) web page about traversal exploits, on a website that is maintained by the U.S. Department of Homeland Security, this is how a path traversal exploit works:
“The software uses external input to construct a pathname that is intended to identify a file or directory that is located underneath a restricted parent directory, but the software does not properly neutralize special elements within the pathname that can cause the pathname to resolve to a location that is outside of the restricted directory.”
The second vulnerability is labeled as critical. The vulnerability was discovered on Friday July 12th by the WordFence team and swiftly fixed by Ad Inserter the following day, on Saturday July 13, 2019.
Authenticated Remote Code Execution
The second vulnerability is called an Authenticated Remote Code Execution (RCE). This allows any user who is registered with the site, with permissions as low as a subscriber to be able to execute arbitrary code on a WordPress installation.
The RCE exploit affects Ad Inserter version 2.4.21 and under.
According to the WordFence website:
“On Friday, July 12th, our Threat Intelligence team discovered a vulnerability present in Ad Inserter, a WordPress plugin installed on over 200,000 websites. The weakness allowed authenticated users (Subscribers and above) to execute arbitrary PHP code on websites using the plugin.
We privately disclosed the issue to the plugin’s developer, who released a patch the very next day.
This is considered a critical security issue…”
Ad Inserter Plugin Reacted Swiftly and Ethically
Almost all plugins and software may contain a vulnerability. What’s important is how quickly a developer responds to issues and how transparent the developers are about it.
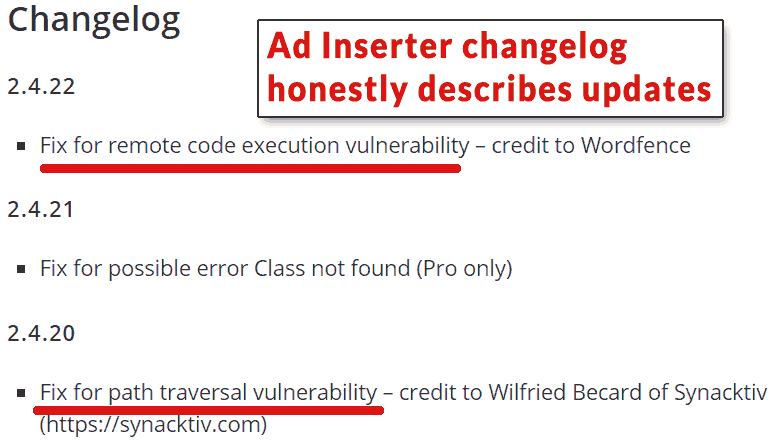
 Screenshot of the Ad Inserter changelog showing that they responded ethically and transparently.
Screenshot of the Ad Inserter changelog showing that they responded ethically and transparently.The Ad Inserter team deserve praise for how quickly they responded and for their transparency about the updates. Ad Inserter alerted their users to the vulnerability through the changelog that is visible on every user’s update page. This is important because it alerts users to the urgency of the update.
The Ad Inserter team acted swiftly and ethically. That’s the best that can be expected from any WordPress developer.
Update Ad Inserter
All users of the Ad Inserter WordPress plugin are urged to log in to their WordPress installation and update their Ad Inserter plugin.
Sorry, the comment form is closed at this time.