26 Jul Hacking Attacks on Elasticsearch and MongoDB via @martinibuster
Unsecured Elasticsearch and MongoDB databases have been targeted in hacking attacks that erase all data. There are no ransom demands.
These are being called Meow Attacks because they leave a telltale meow signature on server log files.
Close up of a screenshot of a log file of a server that was attacked by the Meow
Security researcher Bob Diachenko (@MayhemDayOne) linked to a tweet by Anthr@X (@anthrax0) that was said to represent a screenshot of a log file showing details of a meow attack.
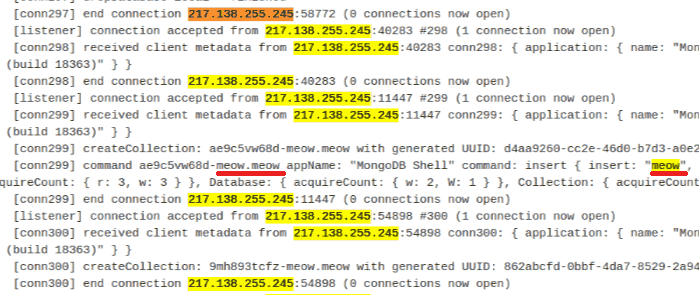
 Close up of a screenshot of a log file from an attacked server that was posted on Twitter.
Close up of a screenshot of a log file from an attacked server that was posted on Twitter.Meow Hacking Attacks
The attacks are targeting unsecured installations of Elasticsearch and MongoDB.
That may mean installations that are not protected by a firewall and are exposed to the public.
That also could be installations that do not have SSL encyrpted communications.
The Elasticsearch hacking attack was noted by security research Bob Chiachenko on July 20, 2020. He noted there were no ransom requests or warnings.
It was an attack designed solely to delete all data.
New Elasticsearch bot attack does not contain any ransom or threats, just 'meow' with a random set of numbers. It is quite fast and search&destroy new clusters pretty effectively pic.twitter.com/F8Ke3CI64i
— Bob Diachenko (@MayhemDayOne) July 20, 2020
The latest high level attack victim is an African online payment service.
yet another victim of Meow attack, Zimbabwe's leading online payments platform. pic.twitter.com/JOQ9kDIJW5
— Bob Diachenko (@MayhemDayOne) July 27, 2020
Automated Hacking Attacks
In general, hacking attacks are automated. A bot script attacks a site by probing for known vulnerabilities such as unsecured ports and vulnerable files. The process is similar to a thief walking down a street checking door handles for unlocked vehicles.
The meow attack is also an automated attack.
What is Being Attacked
Right now, it is unsecured Elasticsearch and MongoDB databases that are being attacked.
Elasticsearch is being attacked the most, followed by MongoDB.
As of July 24, 2020, there were 1,779 Elasticsearch and 701 MongoDB attacks.
There are 1,779 'meow'd' Elasticsearch clusters and 701 MongoDB instances https://t.co/QOG6oAfksy
— Bob Diachenko (@MayhemDayOne) July 24, 2020
Elasticsearch is an open source search and analytics service that is used by companies such as Uber, Shopify and Udemy.
MongoDB states on their website that it is used by companies such as eBay, Adobe, SquareSpace, Verizon and the UK government.
Attacks Alleged to be Hidden by a VPN
Someone on Twitter posted log file screenshots of a Mongo database attack that showed the attacks on that server were going through a VPN IP address in order to hide the true origin of the attack.
The #meow attack is going thru @protonvpn, not sure how many origin IPs there are. From the logs in MongoDB you can see it drops databases first then create new ones with $randomstring-meow @MayhemDayOne@BleepinComputer#infosecpic.twitter.com/49dnVOGyq7
— Anthr@X (@anthrax0) July 24, 2020
ProtonVPN is a virtual private network (VPN). A VPN is a service that masks a users true IP address for security purposes. In some countries they are used to mask their Internet activities from prying governments.
ProtonVPN responded via Twitter by pledging to review the activity and block malicious users who are violating their terms and conditions.
We are looking into this and will block all usage of ProtonVPN which goes against our terms and conditions.
— ProtonVPN (@ProtonVPN) July 27, 2020
Action Recommended
It may be prudent for publishers running Elasticsearch or MongoDB to consider reviewing their installations to ascertain they are secure and not exposed to the public Internet.
Citation
New ‘Meow’ attack has Deleted Almost 4,000 Unsecured Databases
Sorry, the comment form is closed at this time.